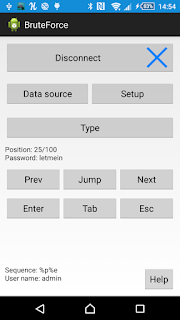
Here's a very simple app that I've recently made for a presentation. It allows to use Android smartphone and InputStick to perform brute force attack (via USB keyboard interface). This is just a simple demo application, not a real "hacking" tool.
With InputStick and BruteForce app, it is possible to perform up to 100 logon attempts in less than 2 minutes (best case scenario, no timeout after unsuccessful attempt). If user picked one of commonly used passwords (like "123456") or easy to guess password, like: combination of user name, number, year of birth, etc. (individual set of passwords can be generated before attack), it is possible that even such a simple attack may be successful. During a short presentation it can be shown how important it is to use following security measures:
- enforcing strong password policy,
- limiting max number of logon attempts (before account is locked),
- adding timeout after unsuccessful attempt,
- limiting physical access to USB ports.
Please note that it is not necessary to install any kind of software on a targeted OS. In most cases, OS will simply recognize new USB keyboard and use generic USB HID drivers. It takes just a few seconds before first password can be typed. Also, even if new USB hardware is filtered, based on PID and VID, it is possible to change the numbers using InputStickUtility app, to match values used by currently connected USB keyboard.
(12.01.2017 - updated download URL)
Quick overview of the app:
Use "Data source" button to select source of passwords:
- 4 digit PIN numbers: 0000, 0001 ... 9999,
- load list of 100 most commonly used passwords (from Adobe leak),
- you can also prepare your own list of passwords and save them to //passwords.txt file. Note: it may be necessary to reboot OS if app is not detecting this file.
"Setup" allows you to:
- prepare "typing sequence",
- decrease typing speed (use if USB host is not accepting fast keyboard input, for example: in BIOS),
- select keyboard layout
Typing sequence can consists of following parameters:
- %p - password
- %u - user name (in such case you must provide it in text field below),
- %e - press Enter key,
- %t - press Tab key,
- %d - 500ms delay.
- %p - type password
- %p%e - type password, press enter
- %u%t%p%e - type user name, press Tab, type password, press Enter,
- %u%e%d%p%e - type user name, press Enter, wait 500ms, type password, press Enter.
Now you are almost ready to go. Plug InputStick into USB port and hit "Connect" button.
"Type" - type currently selected password (or sequence) and go to next one,
"Prev", "Next" - select previous or next password from current set (without typing),
"Jump" - jump to password at selected position (without typing),
"Enter", "Tab", "Esc" - press Enter, Tab or Escape key.